Last year saw an unprecedented number of cyber-attacks against organisations, with over a 200% increase in the number of attacks compared to 2016.
While some attacks have targeted technical weaknesses within systems, increasing anti-virus and malware software is preventing this type of attack from being effective. Where technical attacks have been successful, there is usually an element of human error involved in allowing networks to become infected. As such, attacks now target human error as a way of bypassing security processes in a technique commonly known as phishing.
What is phishing?
Put simply, phishing is an attempt to trick a person into releasing sensitive information. Usually, passwords, bank information and PIN numbers are the targets. However, other details such as mobile phone numbers or information about a company’s management, are also valued targets.
Most people will be aware of phishing through clichéd approaches: emails about a foreign lottery win, a prince who will share his fortune with you or wealth locked up in another country that needs a bank account to be channelled through. While some people still fall for these scams, many are now aware of them. As a result, attacks have now evolved in complexity and personalisation.
Growing sophistication – Spoofing
Where general phishing attacks target hundreds of thousands of people with general information. But cyber criminals are increasingly reducing the number of targets but improving the information about them.
Just as you’re more likely to respond to an email where the sender uses your first name, cyber criminals know you are more likely to click malicious links or hand over data if you think you know with whom you are dealing or communicating. Here are some of the ways attacks work:
Spear phishing – Attacks targeting specific individuals rather than 1000s. For a small amount of research (looking at social media or publicly held records) cyber criminals can construct emails that resonate with staff or create a false sense of familiarity. These are more likely to be opened and acted upon by unsuspecting staff.
Whaling – Targeting of senior company figures or CEO. Attacks will be very well researched, often with several touch points with a company. Cyber criminals may even contact the individual to ‘warm them up’ to ensure that once a phishing email is sent it yields maximum effectiveness. The end goals range from attempts to reveal banking information or, more commonly, passwords that give cyber criminals access to information held on networks and systems.
Clone phishing – Increasing in commonality, these ‘spoof’ emails appear to come from an individual or organisation that prompt the user to take an action. They will take the form of branded, near-perfect copies, of an actual email from a company. Typically, they’ll link through to a dummy webpage also made to look like the real thing that prompts you to enter your login details. Commonly cloned companies include Amazon, Apple, Microsoft and major high street banks such as the below example we’ve recently seen for TSB:
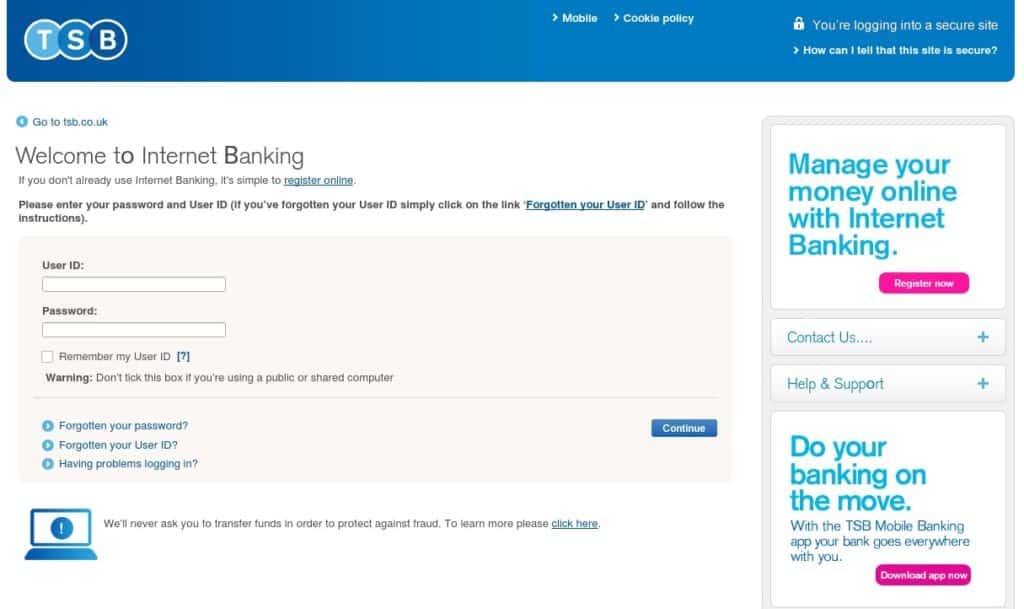
Could you tell what a phishing page looks like?
Clone attacks can also pose as individuals. Once a cyber criminal has obtained a copy of your email style or footer, it’s a 5-minute job to create a clone email account with a very familiar name and look to a senior member of staff. A member of finance contacted at the end of a day by someone posing as the CEO may well be duped into transferring money to an unknown account or giving out sensitive banking details.
Business-email compromise (BEC) – Growing as a risk with the increasing number of devices people own. BEC is when an email account is actually compromised, usually as a result of a lost or stolen phone or laptop. BEC usually occurs because proper security precautions are not in place on the device. Without security such as pin codes, passwords or fingerprint recognition, criminals can get into work systems or send emails that prompt staff to give out sensitive information.
Defence against phishing and spoofing
Without training, approximately 40-60% of staff will click on unsafe links. This is often regardless of how aware they claim to be about cyber threats. Any one of these links could introduce malware to your company’s systems or give away vital company information. Here are the steps we recommend you can take to prevent it:
- Train staff about email and Internet security. Include IT safe practices as part of employment contracts to give it added importance.
- Have an up-to-date firewall appliance to keep malicious attachments out of your network.
- Ensure your email system has a spam checker and link checker – this should help to tackle obviously fraudulent links.
- Hover over a link before clicking it – you should be able to see the URL it’s linking to. If it doesn’t look right, don’t click it.
- Add two-factor authentication on laptops and devices. Users must have a password and their phone to access work systems.
- Encrypt your laptops so that even if they’re lost no-one will be able to get information from them.
- Use apps to partition phones so that, should they get lost or stolen, business information can be deleted remotely.
- Ensure staff feel comfortable to report mistakes if they make them. It’s better to be aware of potential breaches sooner rather than later.
- If in doubt, ask! Whether it’s a case of calling the person who has supposedly sent the email to see if they really want you to transfer cash, or consulting IT experts such as ourselves, make sure you check an email is genuine.
Need more help on understanding what is phishing? Akita is a leading provider of cyber security services. Get in touch for a further conversation:
Contact Us



