
Microsoft Intune Services
Microsoft’s mobile device management solution for ensuring device security
Safeguard Your Operations With Microsoft’s Endpoint Protection Solution
Microsoft Intune is a powerful mobile device management (MDM) solution designed to safeguard and efficiently manage mobile phones, tablets, PCs and wider hardware within your organisation. With a focus on security and ease of use, Intune enables businesses to protect their sensitive data while maintaining seamless device functionality.
Whether you’re concerned about data breaches, regulation compliance, or simply ensuring a secure environment for your workforce, Microsoft’s solution provides the peace of mind you need.
And as a Microsoft partner, Akita can provide implementation assistance and ongoing support to your Intune and wider Microsoft 365 security setup.
For more about adopting Microsoft Intune as your mobile device management solution please get in touch:

Endpoint Security Management
Why Use Microsoft Intune?
With so much information now stored and accessed from mobile devices, they are coming under increasing threat from cybercriminals. Despite unmanaged mobile devices representing a huge security risk, many organisations have no comprehension of what devices are accessing key resources such as email and document stores.
Using Microsoft Intune, any device (including personal devices) that accesses an organisation’s resources can be managed and secured. This means organisations can take control of how their data is accessed. Equally, lost devices no longer pose a GDPR or security risk as information can be wiped from them remotely.
Microsoft Intune Deployment
Our Microsoft Intune Services
Akita can support organisations at all stages of an Intune deployment. This can include any or all of the below:
- Gap Analysis: We’ll conduct a thorough security review of Microsoft cloud systems to pinpoint potential vulnerabilities and establish the scope for the upcoming enhancements.
- Strategic Planning: We’ll hold discussions with stakeholders to evaluate the results of the security audit, devise a strategic approach, and gain consensus on the deployment strategy.
- Policy Consolidation: Based on the agreed strategy, Akita will refine Conditional Access policies to construct a strong security framework that supports – rather than impedes – staff productivity. This includes the introduction of new policies to monitor high-risk activities, the enforcement of Multi-Factor Authentication (MFA), the application of country-specific access restrictions, and stringent checks for device compliance.
- Intune Deployment: We’ll implement new compliance and Microsoft account management policies, focusing particularly on users with administrative privileges. This will also encompass antivirus and firewall settings and the configuration of application control policies to prevent data exfiltration.
- Defender Rollout: Where required, we’ll also undertake a comprehensive rollout of Defender for Endpoint across all devices to ensure robust malware protection and secure device management.
- Enhanced Control Measures: Additionally, we can establish bespoke controls to limit access to administrative portals solely to authorised administrators, effectively preventing access by any non-accredited personnel.
Endpoint Security Management
What Are The Features of Microsoft Intune For Security?
Intune offers an advanced range of features for managing devices. These include:
- Ability to restrict access so only enrolled and compliant devices can gain access to an organisation’s data sources. Restricted applications
can include Exchange or Outlook emails, OneDrive for Business documents, SharePoint Online and more. - Access and policies can be customised based on user/organisation requirements. Devices can be blocked based on
location or sign-on type. - Encrypts organisational data, but not other information: perfect for users accessing data from their personal devices
- Organisational data can be wiped remotely from a device at any time without wiping the entire device.
- Self-service portal can be set up for users to enrol their own devices and install corporate applications across multiple mobile
platforms. - Deploy certificates, WiFi setups, VPN setups and email profiles automatically once a device is enrolled.
- Facilitates limited-use tablets (designed for specific tasks such as reception sign-ins, product catalogues etc.). In limited-use mode,
only apps related to a role can be used on the device.
Cloud Security
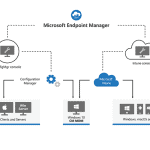
About Microsoft Endpoint Manager
Intune is part of Microsoft Endpoint Manager – a comprehensive cloud management solution. Endpoint Manager can be used to enforce security across your whole cloud estate, and simplify the provisioning and management of devices connected to your systems.
Whether your organisation is interested in a complete Endpoint Manager setup or just wants Intune, Akita can manage the deployment, management and ongoing support of your Microsoft security solution.

